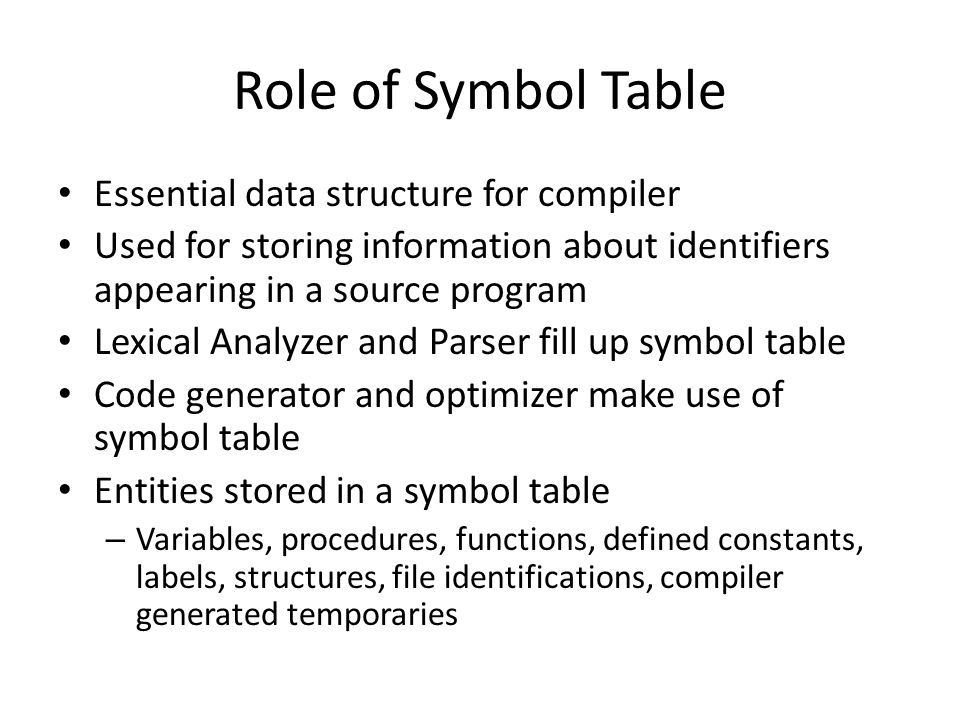
A compiler according to the client's viewpoint is a product that peruses input source records and orders them. The result of the compiler is normally one principal executable document and a few helper records. The compiler ought to be quick and ought to produce improved code.
Yet, for the compiler planner a compiler is a wonderful harmony between information designs and calculations. Both are expected to rapidly check source records, to parse the tokens, to create transitional code, to improve it and to connect modules. Every compiler stage needs the information in some organization. Indeed, even profoundly advanced calculation would be wasteful on the off chance that the information wouldn't be put away productively. Quite possibly of the main datum structures in each compiler is image table.
Image table is an extraordinary information structure that holds all images, from identifiers to inside produced hubs. Compiler image table should contain information structures that will hold string values for image names, number qualities for information pointers, bit values for boolean banners and fields for unique purposes. The association of the image table should be to such an extent that it is feasible to rapidly look for an image, to move to the following one rapidly. to handily add another image at any position, to effortlessly move information starting with one spot then onto the next and not to utilize a lot of memory. At the point when you attempt to consolidate every one of the necessities you will observe that it isn't the case simple to conclude in which structure the information ought to be put away. One of the trade offs is to utilize different image tables for various sort of information.
For instance, the image table that stores the identifiers needs to store strings of variable length with related ascribes proficiently. One of the capabilities most often called during the filtering of the source record is to check whether the identifier is as of now in the image table. The animal power strategy to check all identifiers would be exceptionally wasteful. Subsequently, a superior technique must be found. A typical methodology is to utilize hash tables. There is a hash capability that for every identifier works out some number worth. This worth ought to just rely upon the identifier name. This worth should be force of 2 and scarcely any pieces is sufficient. For each hash esteem there is a different connected rundown of identifiers. So the hash capability decides in which list the identifier will be put away. This way we can limit the hunt count.
- https://subversion.xray.aps.anl.gov/trac/11BMtools/ticket/8841#1Z0-1109-22-exam-dumps
- https://subversion.xray.aps.anl.gov/trac/11BMtools/ticket/8890#1Z0-448-exam-dumps
- https://subversion.xray.aps.anl.gov/trac/11BMtools/ticket/8899#1Z0-517-exam-dumps
- https://subversion.xray.aps.anl.gov/trac/11BMtools/ticket/8901#1Z0-519-exam-dumps
- https://subversion.xray.aps.anl.gov/trac/11BMtools/ticket/8892#1Z0-497-exam-dumps
- https://subversion.xray.aps.anl.gov/trac/11BMtools/ticket/8968#1Z0-829-exam-dumps
- https://subversion.xray.aps.anl.gov/trac/11BMtools/ticket/8895#1Z0-499-exam-dumps
- https://subversion.xray.aps.anl.gov/trac/11BMtools/ticket/8903#1Z0-521-exam-dumps
- https://subversion.xray.aps.anl.gov/trac/11BMtools/ticket/8851#1Z0-133-exam-dumps
- https://subversion.xray.aps.anl.gov/trac/11BMtools/ticket/8694#1Z0-1047-22-exam-dumps
- https://subversion.xray.aps.anl.gov/trac/11BMtools/ticket/8824#1Z0-1087-22-exam-dumps
- https://subversion.xray.aps.anl.gov/trac/11BMtools/ticket/8849#1Z0-129-exam-dumps
- https://subversion.xray.aps.anl.gov/trac/11BMtools/ticket/8735#1Z0-1060-22-exam-dumps
- https://subversion.xray.aps.anl.gov/trac/11BMtools/ticket/8739#1Z0-1064-22-exam-dumps
- https://subversion.xray.aps.anl.gov/trac/11BMtools/ticket/8673#1Z0-1034-22-exam-dumps
- https://subversion.xray.aps.anl.gov/trac/11BMtools/ticket/8906#1Z0-532-exam-dumps
- https://subversion.xray.aps.anl.gov/trac/11BMtools/ticket/8710#1Z0-1053-22-exam-dumps
- https://subversion.xray.aps.anl.gov/trac/11BMtools/ticket/8699#1Z0-1049-22-exam-dumps
- https://subversion.xray.aps.anl.gov/trac/11BMtools/ticket/8764#1Z0-1074-22-exam-dumps
- https://subversion.xray.aps.anl.gov/trac/11BMtools/ticket/8667#1Z0-1033-22-exam-dumps
Another model is image table that, for instance, holds the hubs of program control stream. You should have the option to rapidly move in the two bearings beginning from any hub. This prerequisite infers utilization of two-way connected records.
The most effective way to find out about image tables, hash capabilities, connected records and calculations is to analyze the code of some compiler. You will require a chance to get comfortable with the capabilities and the information utilized however at that point you will have an outline of the entire picture. Each compiler is an ensemble of information designs and calculations.
One such compiler was developed without any preparation. On the off chance that you are keen on the subtleties of image tables you can download the source code. This will be the best book on compiler plan. One more significant field that requirements to comprehend information structures is advanced information recuperation [http://digitaldatarecovery.org/]. To recuperate information from broken plates and undermined record frameworks you want to know how information is put away and what are the relations.